We Live in the Digital Age
Organizations are challenged with putting safeguards in place to protect their valuable digital information. However, the reliance on connectivity in today’s business environment means an ever-increasing pace of data creation and dissemination. As data zaps around the globe in milliseconds, it needs to be shielded. Your network needs to be secure. You need to protect your many sensitive communications, whether in the form of video, voice, or text – not only from criminals, but also from your competitors and any other unforeseen breaches of your network. The need for precaution is further heightened by growing concern for potential damage to your reputation resulting in unknown consequences.
Encryption Protects Your Data
Encryption is the most important privacy-preserving technology available. It protects your data when it's sitting on your computers and in data centers, and also when it's being delivered around the Internet. Implementing encryption is essential and we offer a range of solutions including IPsec, SSL and 128- and 256-bit AES encryption to guard the packets that pass over your various network connections.
You Take Network Security Seriously, and So Do We
In addition to standard encryption, by its nature our technology spreads traffic across multiple Internet connections. Even if an attacker manages to capture one of your individual Internet connections, he will only see a small fragment of your entire traffic. Bonded traffic is authenticated by the receiving server with a hash-based message authentication code (HMAC, from RFC2104). This prevents an attacker from intercepting, modifying, understanding, or forging messages sent between your sites.

Seamless integration with existing network, greater security, and lower costs. A better Internet service.
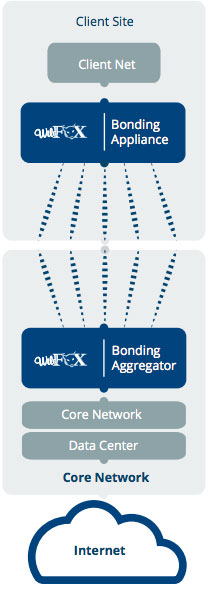
Security Features & Benefits:
- Firewall:
Monitor and control the incoming and outgoing network traffic to identify overall network capacity and enforce entry/exit rules associated with applications.
- Traffic Distribution:
Breaks up sessions into its smallest possible component and distributes the information down multiple connections to add extra layer of security
- Encryption Levels :
Provides comprehensive and affordable protection to secure all communications:
- AES 128
- AES 256
- SALSA20 256
- AES and SALSA20 Tunnel Encryption for Private WANs and IPVPNs.
Bonded Internet™ has the ability to perform standard IPVPN encryption for hub-and-spoke WANs. Customers can choose between three ciphers to encrypt traffic between the CPE device and the Aggregation server (and vice-versa).
- Traffic Authentication.
Bonded traffic is authenticated by the receiving server with a hash-based message authentication code (HMAC, from RFC2104). This prevents an attacker from modifying or forging bonded traffic between the CPE and Aggregation server.
- Seamless Integration with Existing Network Architecture:
Your existing network security design will not be impacted. Multapplied’s Bonded Internet™ supports all encrypted VPN traffic, and is also completely transparent to SSL traffic.
- Encrypted Device Configuration Commands:
Industry-standard SSL protects the appliance from unauthorized control.
- Remote Bonding Appliance (CPE) Security:
The bonding appliance is controlled remotely by our special configuration server. In addition to having its own firewall, all communications between the appliance and the Aggregation server are secured by SSL, ensuring that it is protected.
- On the shoulders of giants:
Our service uses the popular open source Linux distribution Debian. Many contributors around the world work to enhance the security of this operating system, from reviewing code to ensure security issues are eliminated before release, to implementing fixes within hours of a vulnerability becoming known. You benefit from their experience and abilities.
